What is a Hardware Security Module?

A great deal of the way that we interact with the world in our daily lives relies on security. We need to be able to trust that the information we receive is secure and that our personal data remains private. This need for trust and security is critical to many of the day-to-day services we consume whether that be banks keeping our funds safe, retailers handling our payment details securely or social networks keeping our private conversations private.
The simplicity, convenience and ease of use provided by such services belies a critical fact though – creating and maintaining the level of security required is difficult. Organisations that handle personal data are continually under siege from malicious attackers, political activists and aggressive nation states. In fact...
75% of large businesses report having cyber security breaches or attacks in the last 12 months.
One of the key weapons in the arsenal of information security professionals is cryptography. The ability to encrypt data during transmission can prevent eavesdroppers from capturing the data, whilst encrypting data for storage can prevent hackers from gaining access to personal data even if they do break into your network and gain access to your database or file system.
Cryptography can also be useful to prove identity, the HTTPS padlock symbols in web browsers prove that you’re communicating securely with the legitimate website (though there are flaws) and it can even be the basis of a whole new generation of technology in the form of Blockchain, but that's a topic for another day.
The problem with storing keys
In order to use encryption you need to store the keys used to encrypt and decrypt that data somewhere. We're not talking about huge amounts of data, often just a few lines of data in a file somewhere but the problem with storing that data on disk or in databases is that if someone were able to compromise your server or web application they'd have access to your private keys.
To give you a sense of what's at stake here, in June 2020 South African bank Postbank's master key was stolen by rogue employees that were able to gain access to and then print the key. The employees made off with $3.2m but the cost to the bank to replace all of the compromised customer cards is expected to be $58m.
A Hardware Security Module can help to solve this problem in two ways. First it stores the key data on a dedicated hardware device that is tamper resistant. The second primary function of the HSM then is that the device also performs any necessary encryption or decryption using the key on the HSM itself meaning that the key never leaves the device. This means that even if an attacker did manage to compromise your servers, they wouldn't be able to get hold of your actual keys. Advanced features that further improve security are the setup of "m of n" administration where multiple keys are required gain access to the key material on the device.
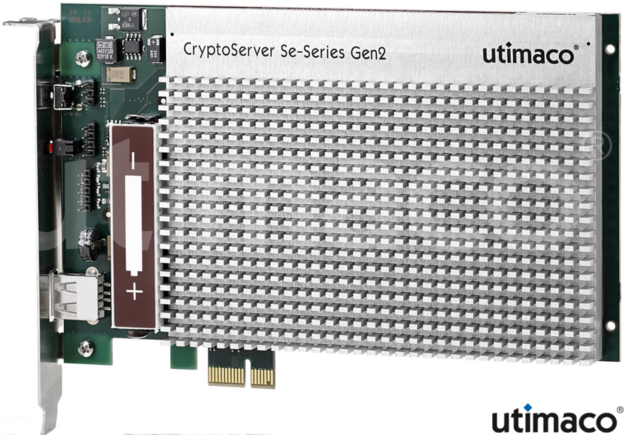
What does an HSM look like?
HSMs come in all shapes and sizes, typically and historically they've been either dedicated hardware appliances, rack-mounted in data centres by organisations but more recently the technology has been made available in small form-factors such as USB sticks and even virtualised in the form of Cloud HSMs.
The examples above show a range of form factors from rack-mounted equipment to server installed cards but the more interesting type for me is really the last one - USB. The professionally curious such as myself aren't easily going to be able to get their hands on $10,000 worth of hardware but the Nitrokey HSM is available for just €69. It provides an incredible low-cost way for developers, security minded users and small businesses to obtain high levels of security at an affordable cost.
What are HSMs used for?
The broad answer is that HSMs could help to improve security anywhere that cryptography is used however HSMs aren't strictly necessary or appropriate in some use cases so they're not in widespread use outside certain sectors. They tend to be found in industries where significant volumes of highly sensitive data are being stored and transmitted such as banks, payment gateways and where the risk of data loss would be high. Example use cases include:
- Handling TLS encryption for web traffic over HTTPS
- Encrypting databases storing sensitive information
- Holding the private keys of a Certificate Authority
- Authenticating user, documents and services
- Storing the private keys for a cryptocurrency wallet or the keys for a private blockchain node.
As part of the Nitrokey Community Programme I've gotten my hands on a Nitrokey HSM 2 so over the coming weeks I'll be testing out a variety of use-cases and software across both Linux and Windows and will be posting back my results.
Update - The first two articles in the series are up now:
Find out more...
The following sources have been a great help to me in preparing this series of articles around the Nitrokey HSM: